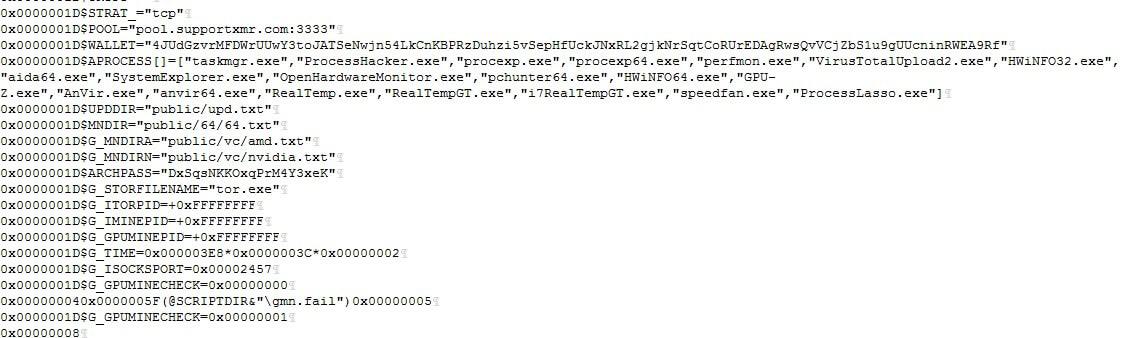
Install – Infect – Mine
The sudden rise of work-from-home models gave enough push to video conferencing apps like Zoom, which were now actively targeted by attackers to exploit the community. Trend Micro reported an incident of hackers exploiting Zoom’s installers, and dumping cryptojacking malware in users’ PCs, along with an original Zoom client to avoid being suspicious. The sudden shift of working models gave little time for companies and users to check for security. This led the download Zoom from unknown sources and an installer for properly setting it up. While they’re getting the Zoom conferencing app as expected, but there’s an infected installer coming along. This was attacked by a cryptojacking malware that users fail to notice. Upon installing, the malware checks for any antivirus software initially, as they could flag the malware and alert user. If unavailable, they proceed with their operations of collecting system data (for compatibility) and minting coins. It collects data like the system’s OS, CPU, GPU, video controllers, etc. These will be helpful to determine how much mining could be done.
Impacts and Remedies
Mining cryptocurrencies takes a vast amount of resources, especially CPU and GPU. Relying heavily on graphics wears out PC sooner than expected. This could even slow down the actual processes needed by the user. And as this minting process runs in the background, the user wouldn’t know anything about it and will see effects in the long term. Installing client and installer software from authentic sources is the only way to avoid being infected. Moreover, having a strong and updated antivirus can help the wave of most of the malware. Source: Trend Micro