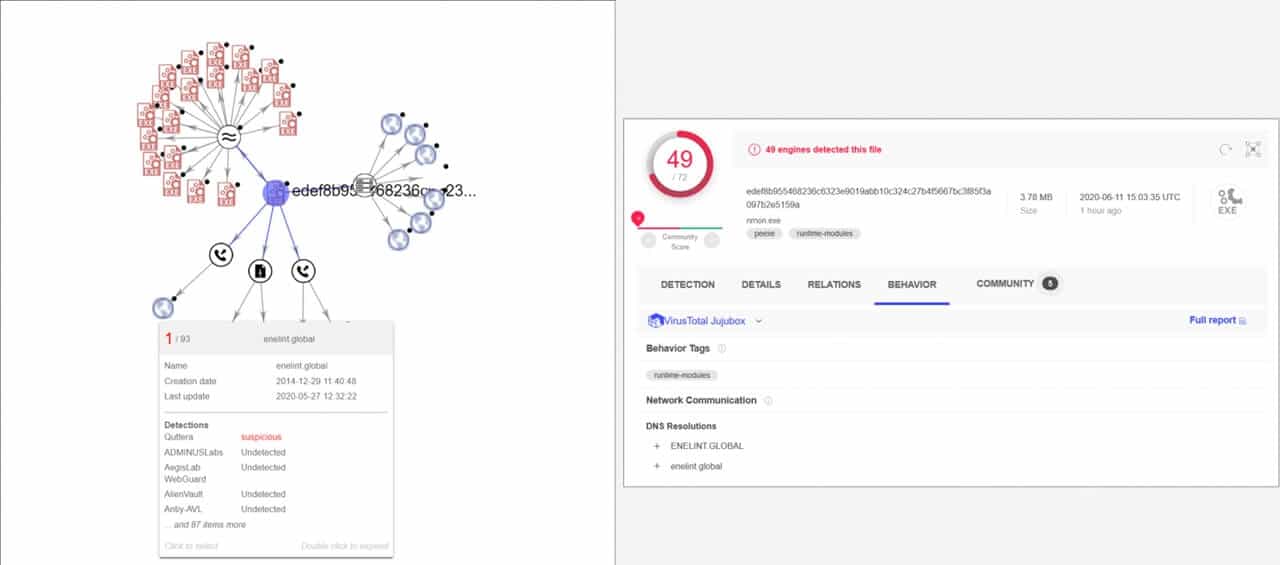
Evaded Risk by Acting Early
Enel Company is a multi-national energy supplier spread across Europe and has reported being targeted by a ransomware attack last week. The company detected the initial attack on June 7th, after its antivirus alarmed about a malicious intrusion. Thus the company separated the corporate systems in order “to carry out all interventions aimed at eliminating any residual risk.” They further stated to have bought back the systems online on Monday morning, after being pulled down on Sunday evening due to attack. And also claims the power plant and other critical services weren’t affected, but some customer IT services due to outage time meanwhile. Enel also assured that no customer data was leaked to any third-party, as they’ve immediately responded by isolating systems. Yet, there’s no clue on how the ransomware operators have intruded into the networks, and whether they accessed or exfiltrated any data. BleepingComputer assumes the source to be through exposed RDP holes, where many ransomware operators intrude. Though the company hasn’t named the ransomware gang behind yet, Milkream, a security researcher identified it to be a Snake group from the samples submitted to VirusTotal. The samples consisted of enelint.global domain, which the Snake ransomware group searches for infecting before encrypting. The domain in question-related to addresses in the US and UK. The authors behind this attack are the same who attacked Honda earlier this week. Via: BleepingComputer