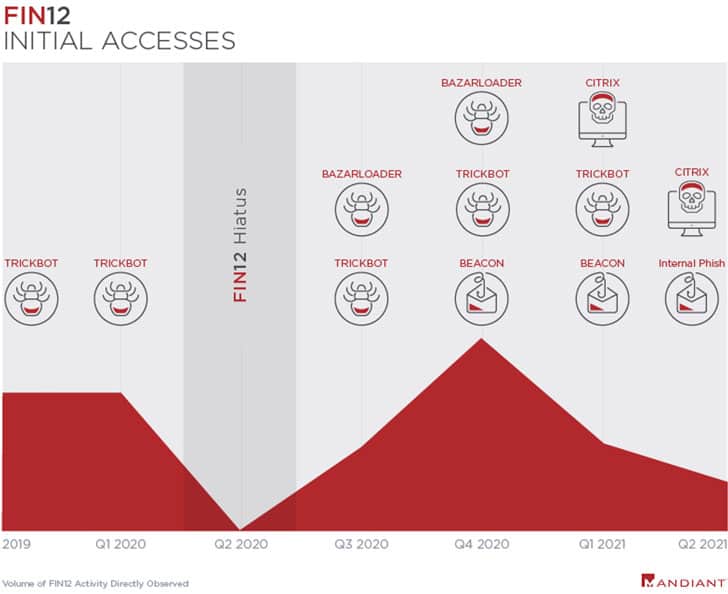
FIN12 is said to be using TrickBot or BazarLoader malware for initial access into the target network, rather than hitting the victim directly through native means. Also, they don’t tend to dump stolen data if the victim doesn’t pay, unlike other hacking groups.
The Russian Ransomware Group in Wild
Out of all the organizations out there, healthcare is considered to be the most sensitive as it deals with patients. And a sudden stoppage of critical services may choke everyone. Thus, they form to be the lucrative targets of ransomware groups. And FIN12 is no different, as they primarily target healthcare services, as reported by Mandiant researchers. They have also noted that the malicious activities of FIN12 against the healthcare industry have increased significantly lately, as they’re aggressively poaching. FIN12 is attributed to a Russian ransomware group, which is also known as UNC1878, and in operation since 2018. It chooses victims based on their revenue, like at least $300 million bar for healthcare targets, and others in education, financial, manufacturing, and technology sectors. And instead of performing every single task by itself, the FIN12 group is said to be leveraging access brokers heavily for quick business. These include BazarLoader and TrickBot, which exploit known and unknown vulnerabilities incorporate devices, and wait for an exploitation plan. If not, they sell this access to third-party ransomware groups who set in their payload for further exploitation – encryption and extortion. FIN12 does the same, as they buy access from TrickBot or BazarLoader and deploy their payload – which is said to be similar to Ryuk’s. While the FIN12 gang is financially motivated, they don’t follow the suit of others like dumping the stolen data for the public if the victim refused to pay. Also, they’re found using publicly available offensive tools like Cobalt Strike beacons for post-exploitation activities.