Analysts believed the future would mostly be of remote working, but not this early. The ongoing pandemic has forcefully drawn corporates, educational institutions, churches, etc. to video conferencing apps to complete their chores anyway. This led platforms like Zoom, Microsoft’s Team, Cisco’s WebEx, etc. to serve them. But, they aren’t prepared for this sudden uprise of dependency, thus still discovering and patching the loopholes found now and then.
A Simple Social Engineering Attack!
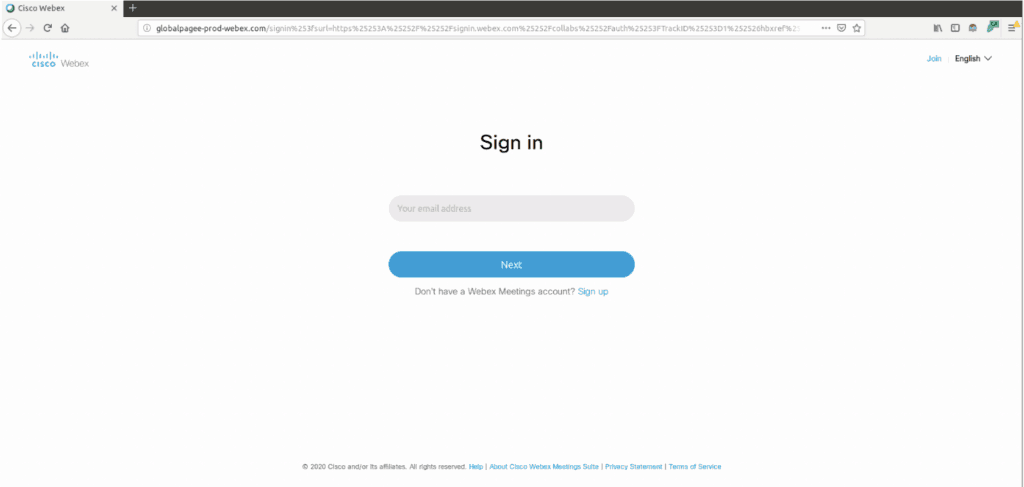
Cisco’s WebEx story isn’t about a flawed software, but the user’s ignorance. They fall prey for phishing attacks and foolishly submit sensitive details to sites that aren’t genuine, and cry for losing money later. Here’s a story by ThreatPost explaining a story of such. Phishing attackers are actively exploiting the popularity of WebEx by sending emails to users as fake Cisco Security Advisory. They chipped in an old Security Advisory note from 2016, where a flaw in Docker Engine was discovered and patched then itself. But it was now used by attackers to feed fear in users as this vulnerability, if not repaired, shall allow hackers to access admin privileges. Though it’s true, it’s repaired already. But they still prompt the user to update the WebEx client, as their only saving option. Here, they direct the user through a fake sign-in button, which takes them to a fraudulent website crafted by attackers. The website is closely resembled Cisco’s WebEx sign-in page and asks the user to login with their credentials. Entering the email address and sensitive password will be captured and sent to the attacker’s C2 server. These will be used for further exploitations or sold bulky in dark web forums later. Its counterpart, Zoom, on the other hand, is facing enough backlash for uncontrolled Zoombombing, privacy issues, and data sharing scandals. Just as WebEx, Zoom, to has seen a surge in its subscriber growth from 10m to 200m daily users, pushing its stock up to five-fold already. Via: ThreatPost