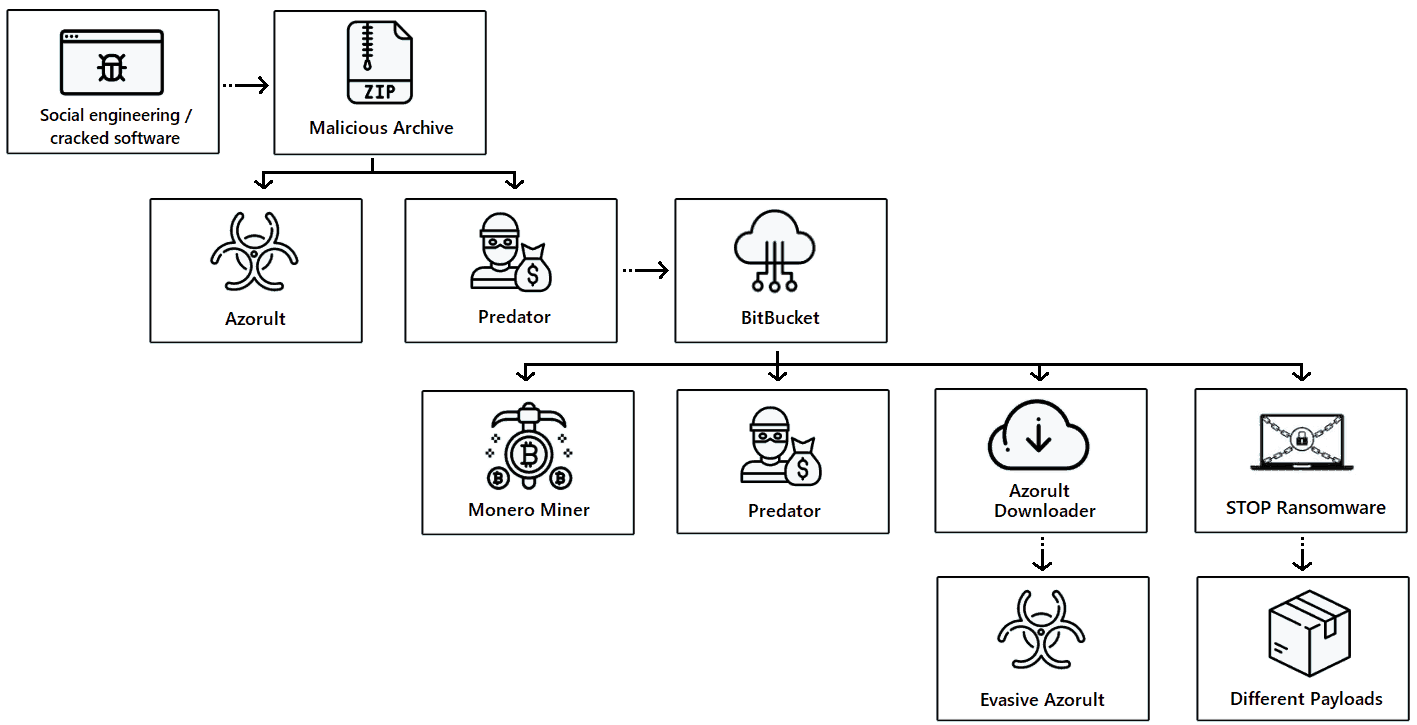
As described by a CyberSecurity firm called Cybereason, a new threat actor in the wild is actively exploiting devices by dumping malware through BitBucket. BitBucket is a repository hosting service for source codes. This platform is used for updating the malware constantly for further improvements in stealing.
According to Cybereason, the malware dump attackers are setting consists of:
Predator: An information stealer to steal credentials from browsers, using a camera to take pictures, screenshots, and steals cryptocurrency wallets. Azorult: Which is also an information stealer that steals passwords, email credentials, cookies, browser history, IDs, cryptocurrencies and has backdoor capabilities. Evasive Monero Miner: A dropper for a multi-stage XMRig Miner to mine Monero cryptocurrency. STOP Ransomware: Based on open-source ransomware platform, it’s used to ransom the file system. Moreover, it can also download additional malware for further infection. Vidar: It’s an information stealer that steals web browser cookies and history, digital wallets, two-factor authentication data, and takes screenshots. Amadey bot: A simple trojan bot primarily used for observing and collecting information. IntelRapid: A cryptocurrency stealer for stealing different types of cryptocurrency wallets
Steps in dumping payload. Source: Cybereason All these malware aren’t dumped all at once but by stages. Here, the BitBucket is leveraged for updating the primary malware and to install additional payloads. Researchers say that there’s are tens of thousands of malware counts and are being updated every three hours! This led more than 500,000 systems to be infected by now, and are going on actively. The cryptocurrency wallet and other sensitive information stolen is sold in dark web forums, which could garner the sellers (attackers) millions. Source – CyberReason | Via BleepingComputer